Authenticating AIS and VDES Keeping them safe for another generation of mariners
Over the last ~20 years, the internet became part of our daily lives; used to access bank accounts and pay our parking tickets. As we began to send more of our personal data over the internet, we all became aware of the need to secure the data we send and receive; whether by looking for the padlock symbol next to a web address, or using more sophisticated multi-factor authentication systems for our bank and workplace. And to help us, the common internet protocols we all use today will routinely secure all data sent over them… and in those rare circumstances where we don’t use secure protocols, we know that we really should be using them!
Whilst we are now familiar with internet security, there is less understanding of radio security, particularly for the low level data communication protocols used for sending maritime data. These protocols include the Automatic Identification System (AIS) as used today, as well as new and future systems, including the VHF Data Exchange System (VDES).
Historically, security for maritime radio systems was provided by accessibility; radios and AIS transceivers were niche and expensive items, often with restricted sale in some jurisdictions. Consequently, they were out of reach to many actors with malicious intent, and even if more sophisticated bad actors did obtain them, whilst they could be used to cause nuisance, it was harder to cause serious harm.
However, this situation is changing. New technologies such as digital navigation systems and maritime autonomous surface ships (MASS) mean the mariner (and those ashore) are increasingly using, even relying upon, radio data communications. The introduction of these new systems, and an increasing reliance on existing ones, such as AIS, means that spoofing them may not simply present a nuisance, but can cause much more serious harm. Furthermore, spoofing them is becoming easier and cheaper. Cheap hardware, including software defined radios (SDR), capable of transmitting anywhere in the maritime spectrum is now freely available along with open source software that allows users to spoof maritime messages with a minimum of expertise. This is typified by the hardware shown in Figure 1.
As such technology becomes more widespread, it is quite conceivable that it is only a matter of time before dedicated (illicit) devices become available allowing users to easily spoof a range of AIS and other data messages at the push of a button; perhaps intended to help mask illegal activities, but capable of much more nefarious uses.
Such dangers of spoofing to maritime navigation and data communications have been recognised by IALA. IALA recommendation R1024 Cyber Security for the IALA Domains, published in December 2022, states: ‘that IALA members work towards the goal of ensuring all data in the IALA domain is provided with a means to authenticate the data’.
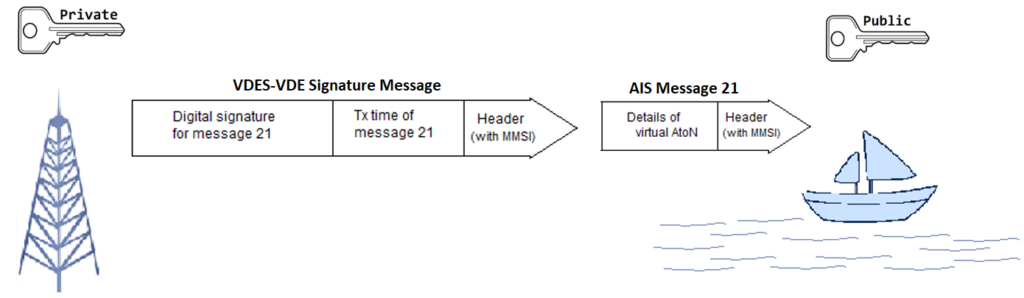
To support this, the General Lighthouse Authorities of the UK and Ireland (GLA) have developed a backwards compatible authentication system to secure AIS and VDES and prevent spoofing. The system works by using public key cryptography (PKC) to generate ‘digital signatures’. These digital signatures are broadcast immediately after an AIS, VDES or other data message (a process shown in Figure 2) and can be used to provide categoric proof that messages are genuine and come from the maritime authority or entity they purport to come from, and not an imposter.
Our work has shown this is a viable approach and the results from live broadcast trials have been published and presented to groups including IALA (at the 20th IALA conference in Brazil) and the IMO/ITU Joint Experts Group on Maritime Radiocommunication Matters; feedback from all of which has been very positive.
Consequently, to help realise AIS and VDES authentication, IALA DTEC Working Group 3 is currently drafting a Guideline on VDES Authentication Techniques based on our work. We therefore invite all IALA members with an interest and expertise in these matters to provide input to the guideline via the working group.
Using the above technique, the GLA look forward to being able to authenticate all our AIS and other messages as a matter of routine, thereby keeping our services safe to use for another generation of mariners, human or machine.


Author: Gareth Wimpenny
Rapporteur: Paul Ridgway
